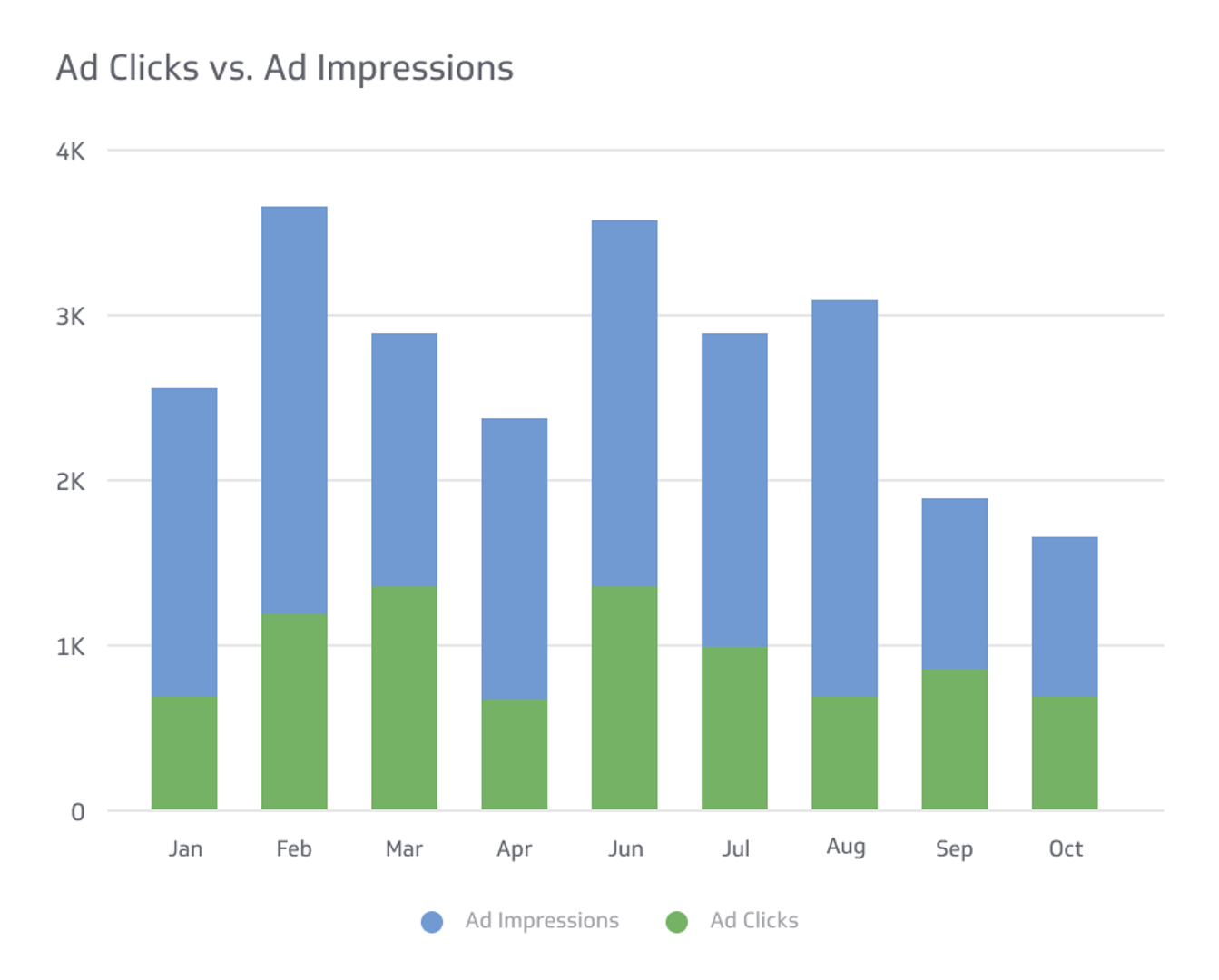
Clicks limits access to customers' personal data after cyberattack
Por um escritor misterioso
Descrição

14 Types of Phishing Attacks and How to Identify Them

12 Cyber Security Measures Your Small Business Needs

How companies can secure and protect customers' personal data
/cloudfront-us-east-2.images.arcpublishing.com/reuters/CUXAHHXCLRNX7AIU5APRCKWY4A.jpg)
Montenegro's state infrastructure hit by cyber attack -officials
What is data privacy and why is it important?

8 Steps to Reduce the Financial Impact of Data Breaches to Your
AI Cyber-Attacks: The Growing Threat to Cybersecurity and

Phishing attacks: defending your organisation
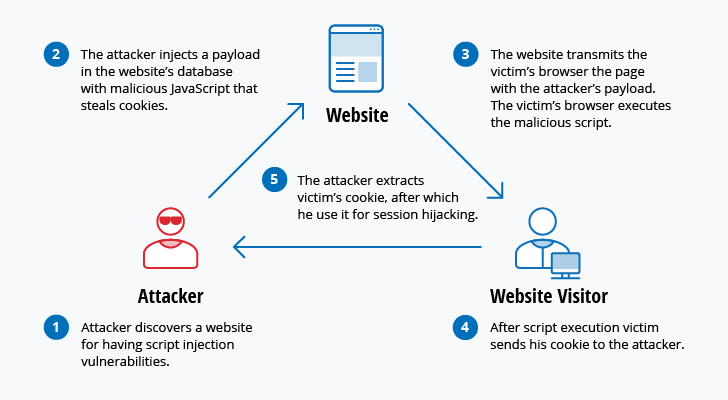
The 12 Most Common Types of Cybersecurity Attacks Today

eCommerce Security: A Complete Guide to Protect Your Store

Cyber Attack Survival Manual: From Identity Theft to The Digital

Cybersecurity 101: Everything on how to protect your privacy and
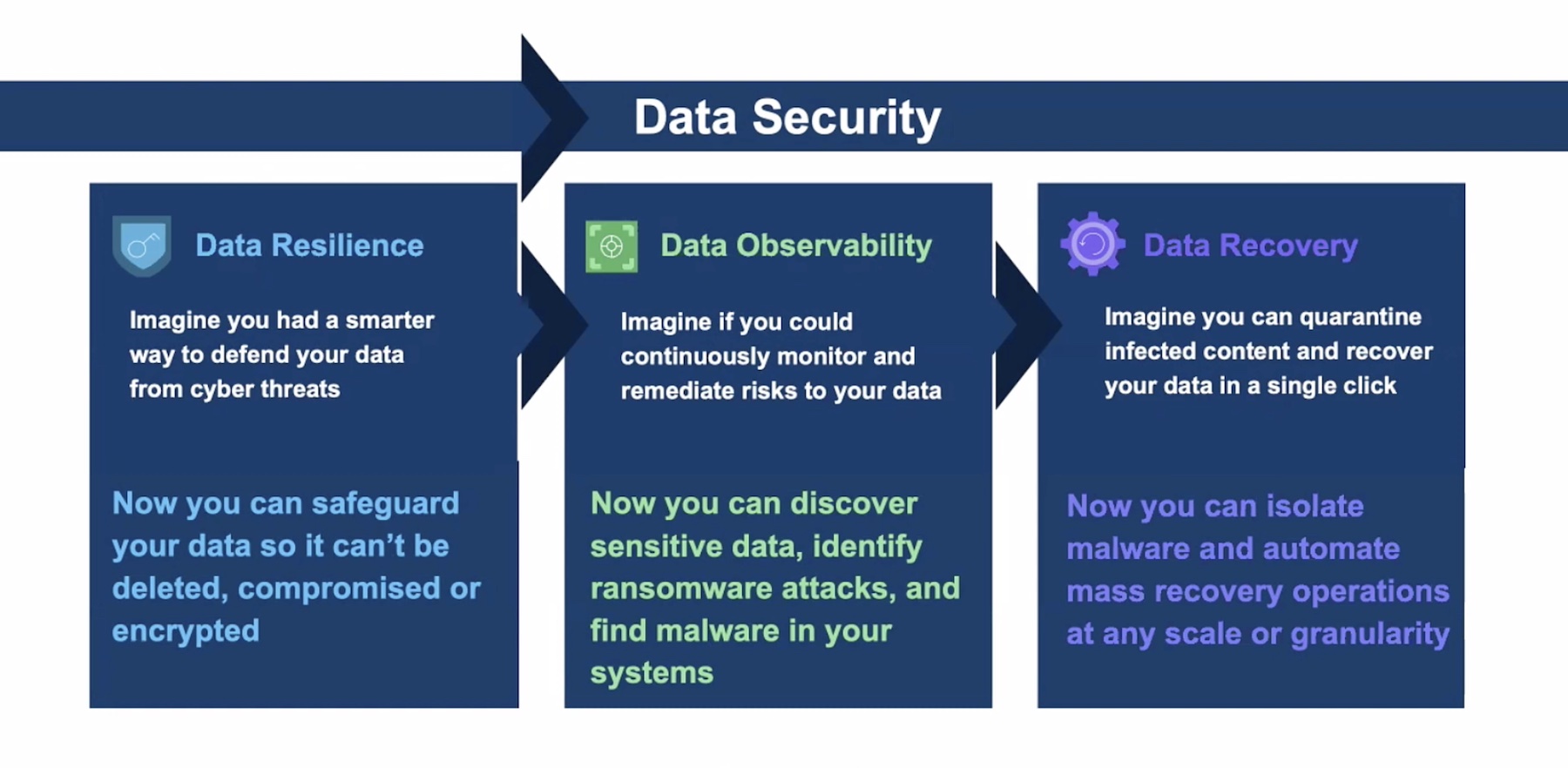
Securing Classified Data with Rubrik and Zscaler - Gestalt IT

M2 Technology Solutions
de
por adulto (o preço varia de acordo com o tamanho do grupo)