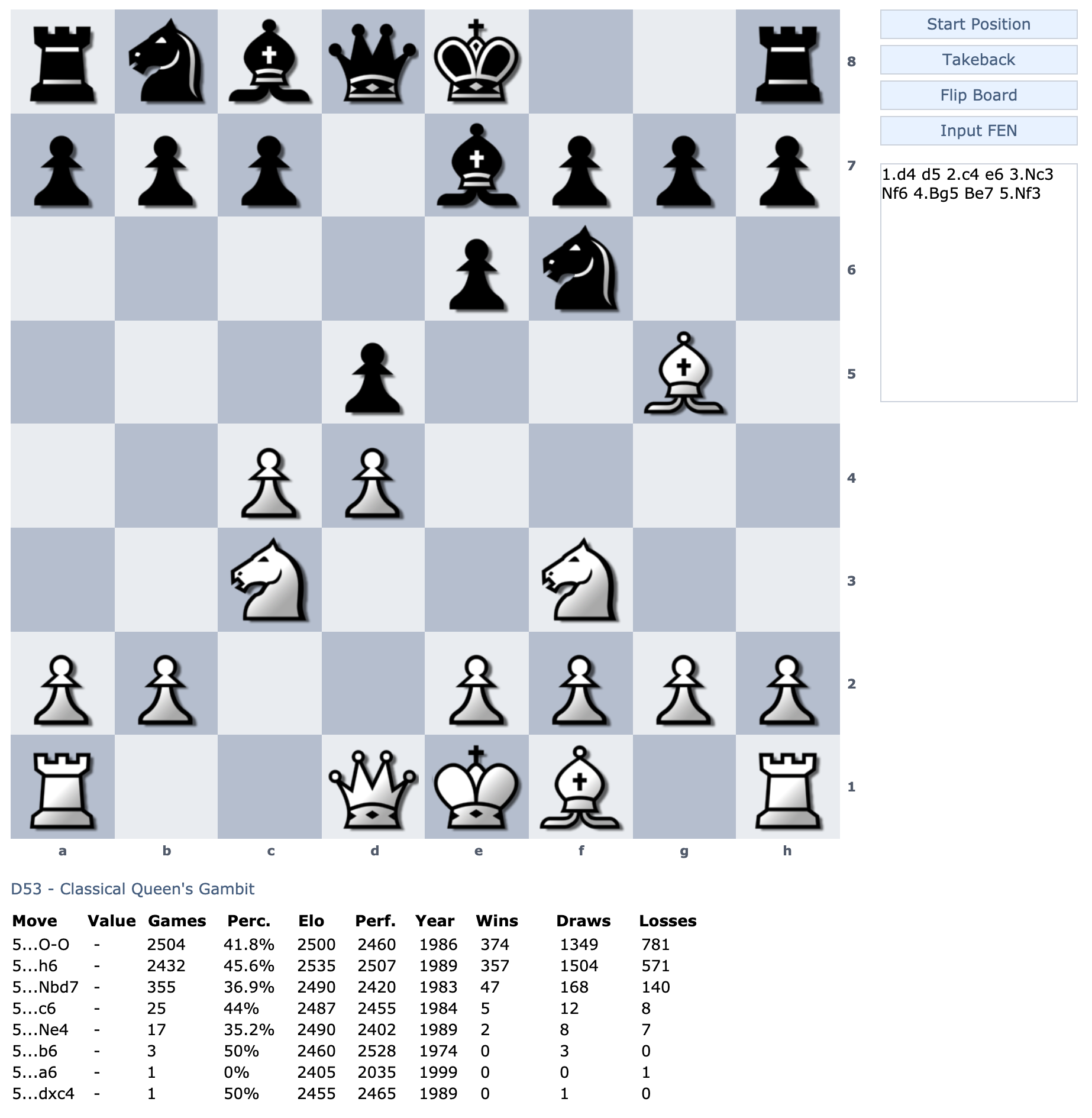
The Unacceptable Flaw with : Use of Game Explorer/DB in
Por um escritor misterioso
Descrição
DO YOU REALIZE THAT YOUR TURN BASED OPPONENT CAN LEGALLY PLAY THE WORLD'S BEST CHESS MOVE AGAINST YOU FOR THE ENTIRE OPENING? That as long as you stay in book (which means making a good move), they can choose the most preferred move from the collection of Masters and Grandmasters since the 1800s against

Deep Dive into Real-World Kubernetes Threats

DB Electrical Sfd0049 Starter For Ford Explorer 4.0L
:max_bytes(150000):strip_icc()/51-attack.asp-final-b97e967390ea40028ff9ddf30d2ee6c5.png)
51% Attack: Definition, Who Is At Risk, Example, and Cost
Inventory – Minecraft Wiki

Building Interactive Enterprise Grade Applications with Open AI
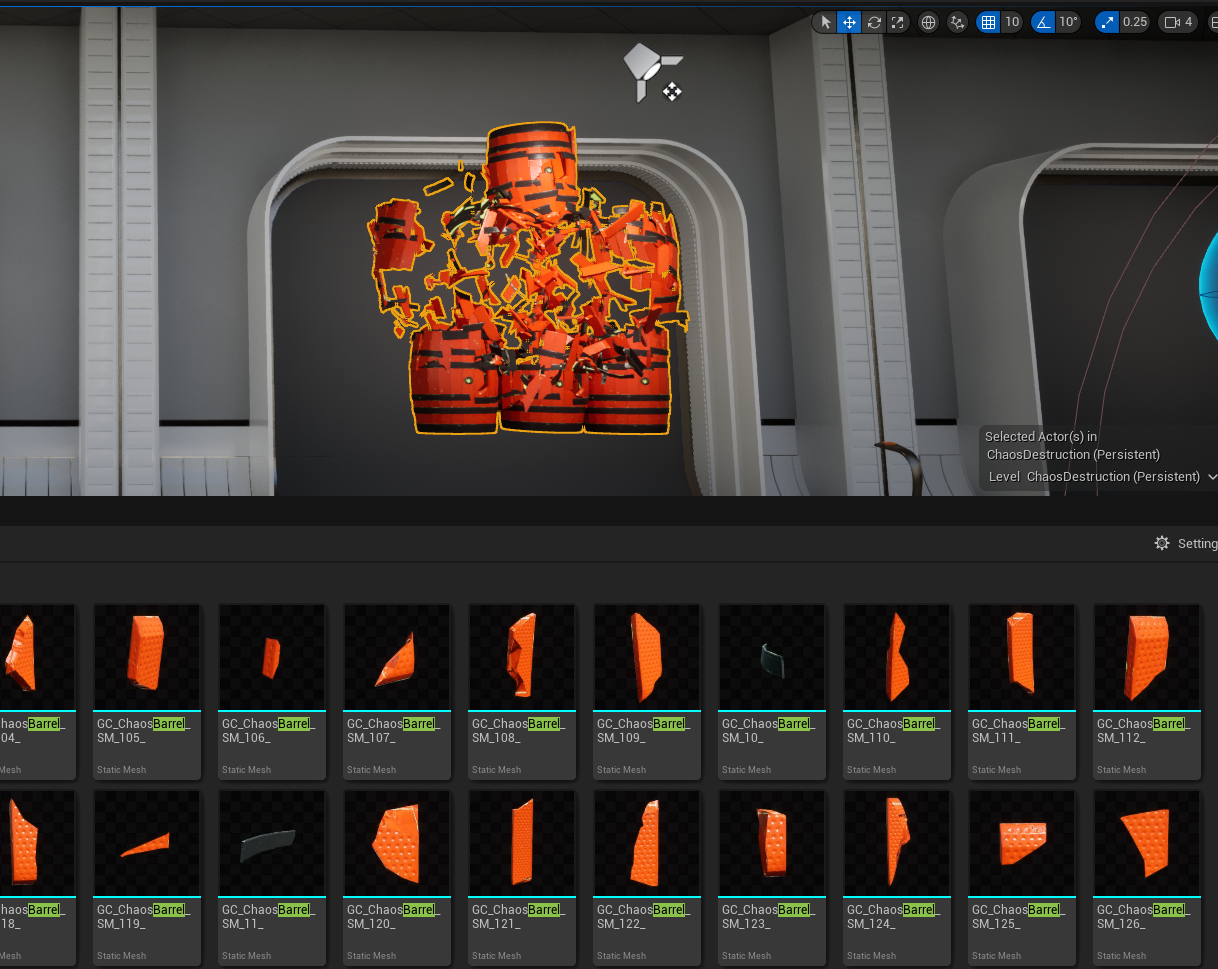
The critical flaw of asset browsers, by Robin-Yann Storm

What if a few inbox Windows apps got a bit of a redesign with

The Web3 Movement's Quest to Build a 'Can't Be Evil' Internet

Two Deck Formats: Is Wizards Neglecting Constructed? • MTG DECKS
Highlight, take notes, and search in the book

Art of Software Security Testing, The: Identifying Software Security Flaws: Identifying Software Security Flaws
de
por adulto (o preço varia de acordo com o tamanho do grupo)