The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Descrição
The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.

9 stages of ransomware: How AI responds at every stage

SpiKey technique allows opening the lock by recording a turning key

Segmentation, trace denoising and spike extraction framework. (A) Mask

Why are mRNA vaccines so exciting? - Harvard Health

6 fintech investors sound off on AI, down rounds and what's ahead

SpiKey technique allows opening the lock by recording a turning key
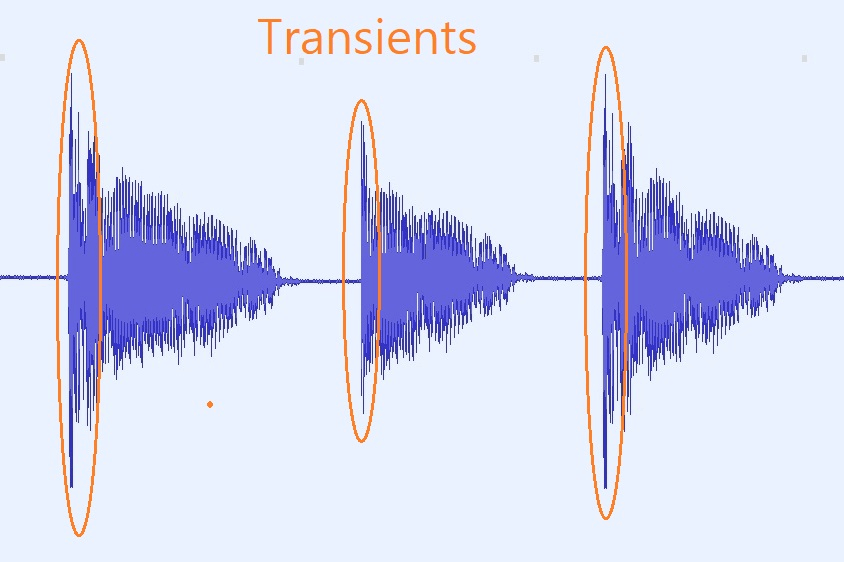
What are transients? How to deal with it in the mixing proces?

Hackers can now clone your keys just by listening to them with a smartphone

What is Peer to Peer Network, and How does it work? [UPDATED] - Blockchain Council

Vengeance Sound
de
por adulto (o preço varia de acordo com o tamanho do grupo)







:strip_icc()/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2023/s/s/MoKn15TfWJbvEOlB4c1Q/mundial-fifa-23.jpg)