Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
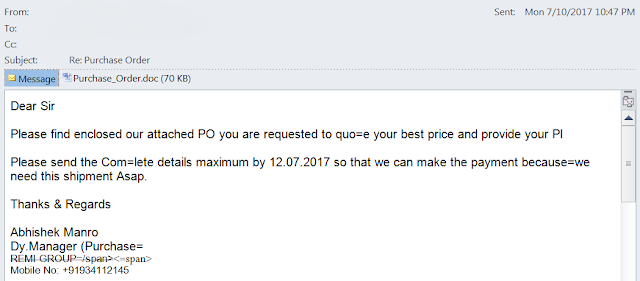
When combining exploits for added effect goes wrong
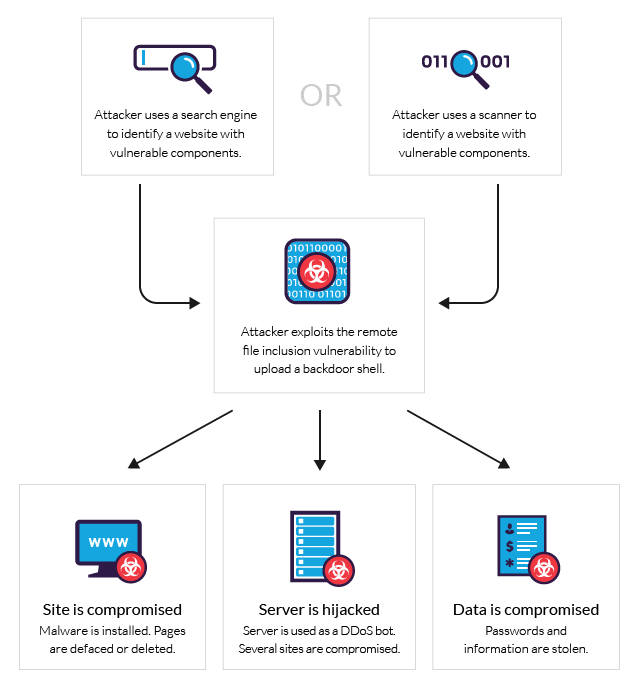
What is RFI, Remote File Inclusion Example & Mitigation Methods

File Inclusion/Path traversal - HackTricks

Analyzing patterns and signatures of an exploit using Wireshark – November 17, 2023
How to Exploit Remote File Inclusion to Get a Shell « Null Byte :: WonderHowTo
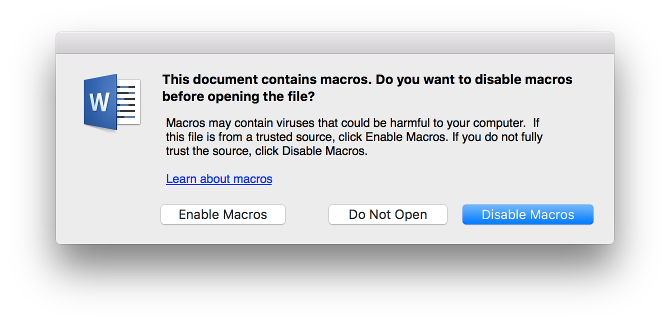
Who Needs to Exploit Vulnerabilities When You Have Macros?
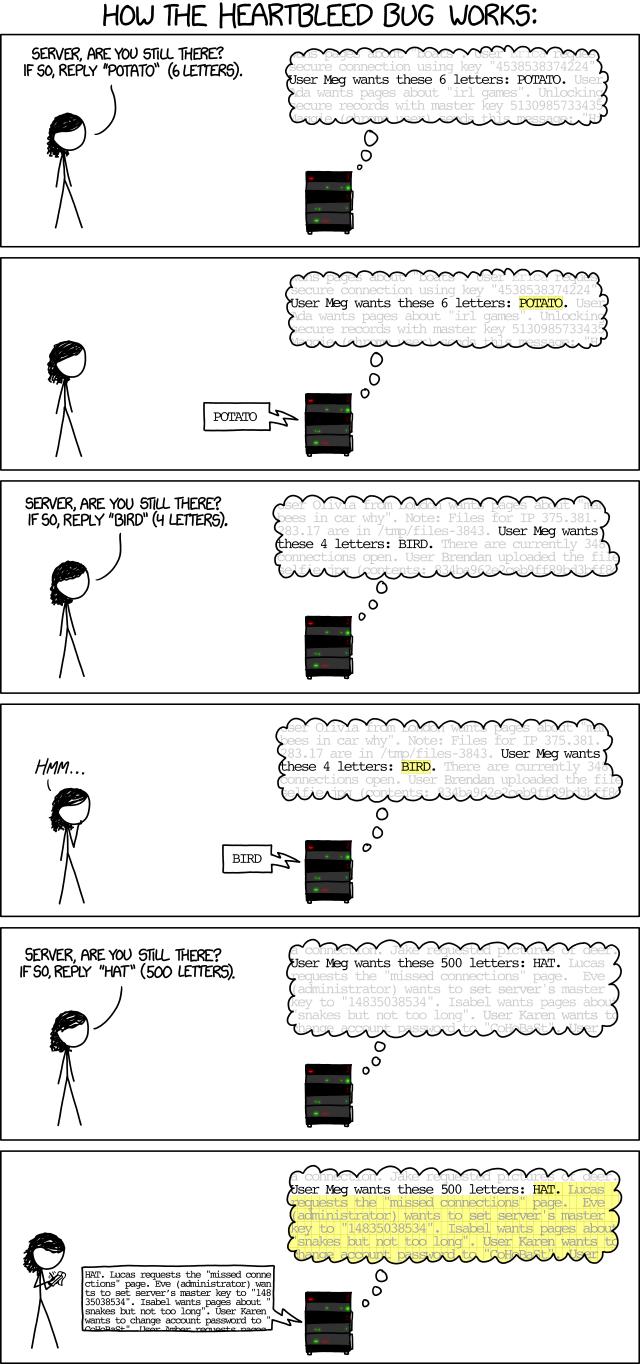
Heartbleed SSL Security Exploit - Super Tech Crew
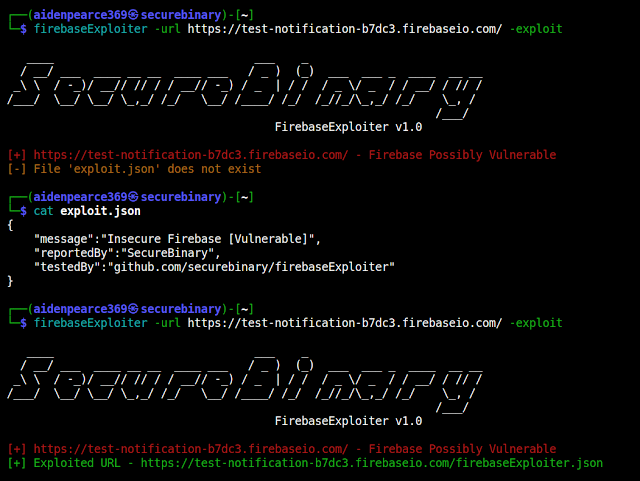
FirebaseExploiter - Vulnerability Discovery Tool That Discovers Firebase Database Which Are Open And Can Be Exploitable

Traders' dollars in danger: CVE-2023-38831 zero-day vulnerability in WinRAR exploited by cybercriminals to target traders

WinRAR zero-day exploited since April to hack trading accounts
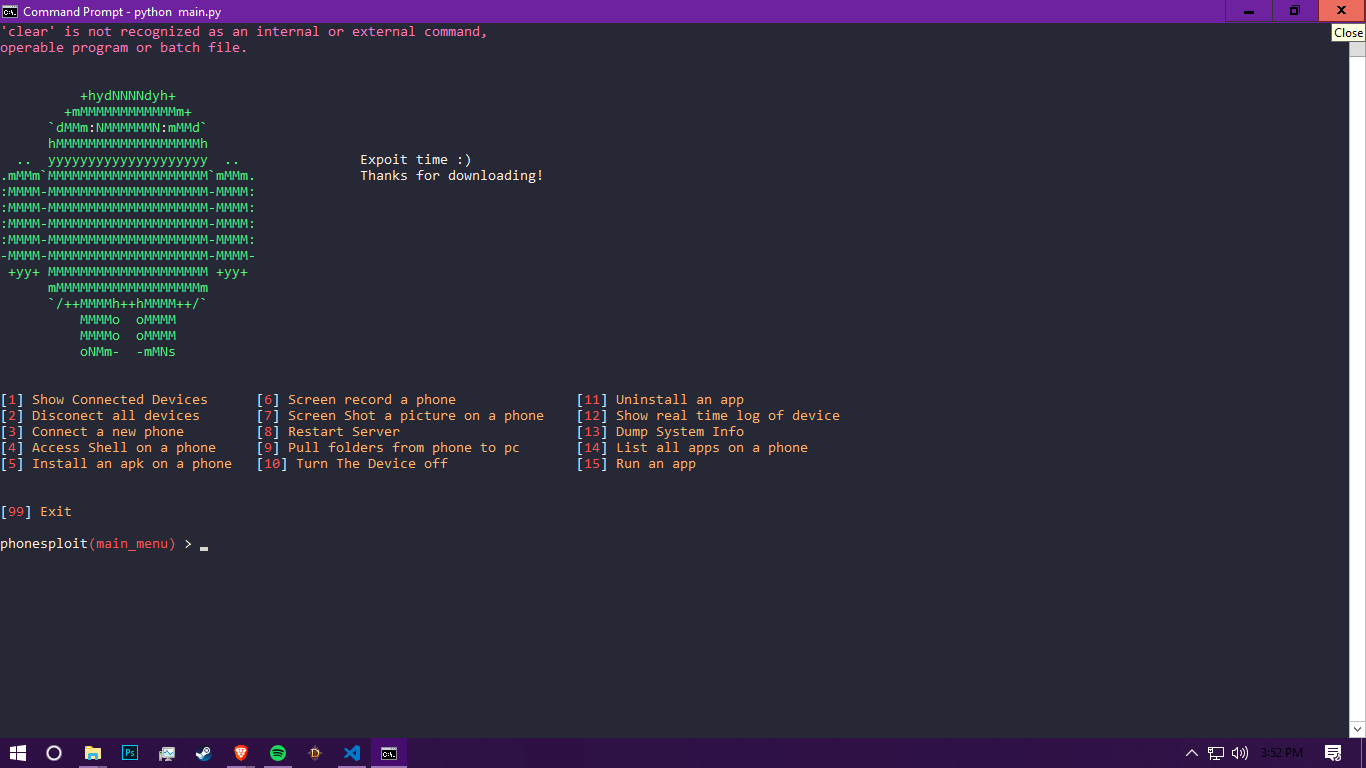
PhoneSploit v1.2 - Using Open Adb Ports We Can Exploit A Andriod Device
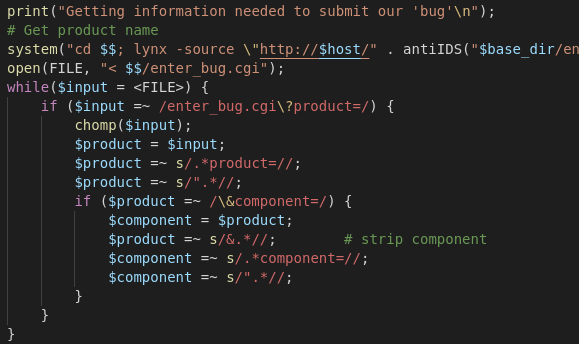
Exploit Wars II - The server strikes back
de
por adulto (o preço varia de acordo com o tamanho do grupo)